Bio Authentication and Its Importance for Your Business
Biometric authentication is a unique verification system that utilizes specific biological characteristics of the user to verify the genuineness prior to allowing accessibility. It compares the captured data with stored data to confirm user authentication in the database. If both the data match, the authentication stands confirmed. Such verification processes are mainly used to control accessibility in physical and digital resources such as buildings, offices and computer devices.
Types of Biometrics
It is the era of advancement in technology with a new upgrade in software or gadgets. Biometrics, which was limited to science fiction, has made its way to business organization. Different types of biometric authentication are:
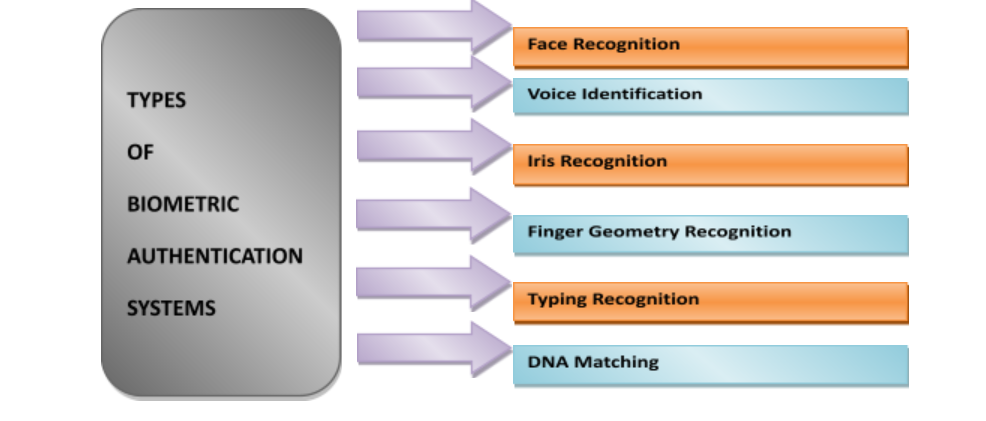
Why do Businesses Need Biometric Authentication?
Biometrics have gained popularity as a more secure form of authentication , as a result of which, companies across the globe are using this to protect assets as well as secure their users’ data. Having provided a more dynamic solution to the business owners, bio authentication is required because,
- It provides operational efficiency. The resetting of forgotten passwords can be a cumbersome task for the operations department or the customer service department. Since the biometrics are bound to remain unchanged, this mode of verification saves time and money as well as resource consuming operational tasks.
- Since it is difficult to duplicate the physical biometrics such as fingers, iris or voice, this tool serves as an excellent addition to the organization’s access control systems. This ensures accurate identification and accountability. The biometric systems create a considerable audit trail for user transactions, making it convenient and versatile.
- This system of verification is entirely user friendly and does not require any prior training. It guarantees prolonged security for the business.
- These are scalable and many versions of this system can be used depending upon the business requirements. For instance, during the start-up phase, a company can use the discrete features of this authentication system, while at a higher level, more sophisticated features can be used.
- Biometric authentication is a cost-effective investment as your firm can keep a tag on the management time and costs.
- The effect of any fraudulent activity can be easily assuaged.
- The system avails the businesses with multiple verticals. Bio authentication allows user identification with high accuracy even with most crucial data like finance or government details.
Bio Authentication vs Passwords
The business world has been buzzing with the preference of bio authentication over the conventional password security systems. Let us compare the two and understand why the former is preferred over the latter.
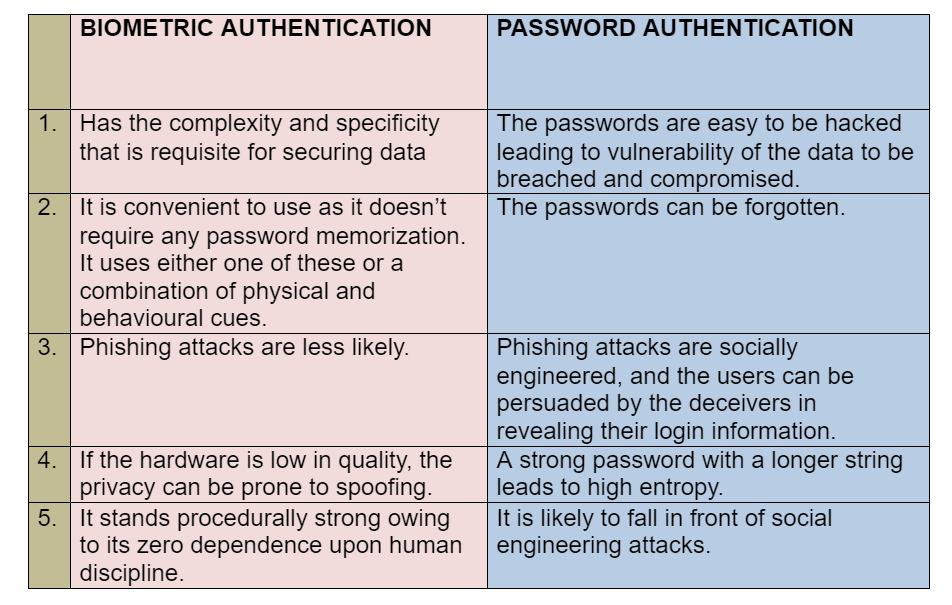
Even though biometrics has excelled and has become a key aspect in the leading organizations today, some less contemplated disadvantages of this cannot be ignored.
- Unlike the conventional security systems, in view of the account getting compromised, which is rare, the originally configured security access cannot be altered without physical access.
- In a rare case scenario, if a hacker has been able to replicate your biometrics, such as by using a phony fingerprint, the characteristics remain immutable.
- In some cases, this system of authentication has been known to show delays in the verification process.
NAVOMI’S BioAuth
NAVOMI has come forth with its unique channel agnostic biometric authentication system called BioAuth, which authenticates the users with their voice recognition. This bot is deployed via WhatsApp. It authenticates the users and can extend to human agents as per the users’ requirement.
Even though it carries its own share of negative aspects, the shortcomings of bio authentication are usually due to a poor-quality hardware. The fact that it is gaining extreme popularity and credibility among business organizations cannot be ignored. Biometrics can elevate a company’s growth to newer levels by reducing or nullifying prevalent security threats.